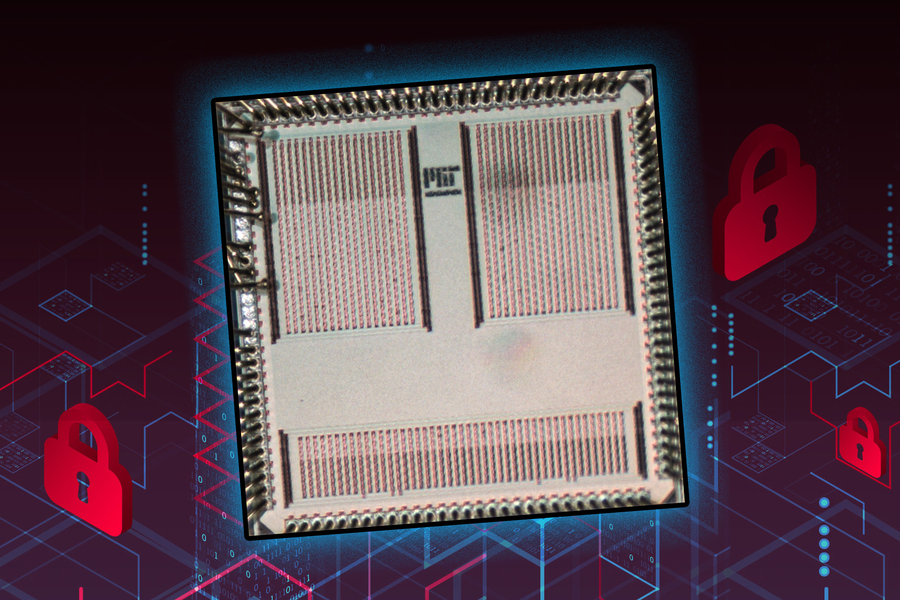
MIT Researchers Develop An ASIC To Defend Against Power-based Side Channel Attacks
A team of researchers affiliated with MIT School of Engineering, Indian Institute of Science, and Analog Devices have collaborated to design a tiny application-specific integrated circuit (ASIC) to defend against power-based side-channel attacks on an IoT device. Before getting into the details of the ASIC, let us first understand what are side-channel attacks. Side-channel attacks try to obtain secret information by exploiting the system or the hardware using channels such as sound, heat, time, and power consumption. Power analysis is a branch of side-channel attacks where power consumption data is used as the side channel to attack the entire system to break the secret key of the cryptosystem.
Most of the existing methods to prevent these side-channel attacks are power-intensive and demand more power which is not feasible for edge AI devices that are deployed in remote areas. The group developed an ASIC that can defend against power side-channel attacks while using less energy than common security techniques. Also, thanks to the minimalistic design with a size smaller than a thumbnail make it convenient to be integrated into edge devices and wearables to perform secure machine learning computations.
The goal of this project is to build an integrated circuit that does machine learning on the edge so that it is still low-power but can protect against these side channel attacks so we don’t lose the privacy of these models,” says Anantha Chandrakasan, the dean of the MIT School of Engineering, Vannevar Bush Professor of Electrical Engineering and Computer Science, and senior author of the paper. “People have not paid much attention to the security of these machine-learning algorithms, and this proposed hardware is effectively addressing this space.
The technique used to prevent some side-channel attacks is known as threshold computing. Unlike the neural network processing on the data, the data is first split into unique and random components which are then operated individually in random order. Due to randomness, the information leakage is reduced as it does not reveal the actual side-channel information. However, as it sounds, the approach is more computationally expensive and requires more memory to store the random ordered information.
To optimize the whole design flow, the researchers developed a function that reduces the multiplication of the neural network to process the data which in turn requires less memory. The neural network model parameters are also protected by grouping them before encryption to provide more security while reducing the amount of memory required on the chip. Sometimes, these model parameters can help hackers to gather information impacting the integrity of the system.
By using this special function, we can perform this operation while skipping some steps with lesser impacts, which allows us to reduce the overhead. We can reduce the cost, but it comes with other costs in terms of neural network accuracy. So, we have to make a judicious choice of the algorithm and architectures that we choose.
Maji says.
The team revealed future work and hopes to implement the approach to electromagnetic side-channel attacks as they are hard to defend because the hacker does not need the physical device to collect the information. The work is being presented at the International Solid-States Circuit Conference.