Since Internet of Things market is growing exponentially and the use of embedded and pervasive devices is increasing, this may introduces some security threats in the network.
A group of Spanish researchers at the Computer Security Lab, Universidad Carlos III de Madrid have developed a malware, ArduWorm, that targets Arduino Yún, a common platform used in IoT. This malware can bypass all the security provided within Arduino by causing a memory corruption. According to the researchers this malware will be “able to get the control of a Linux-based microprocessor integrated in the device with full privileges, which allows it to install a backdoor and spread as a worm through the compromised network”.
Modern smart devices such as smart phones or tablets are used in social networking, instant messaging or e-commerce. Therefore, these devices store a huge amount of personal and valuable information that is attractive for attackers.
Arduino Yún, is an Arduino board that was specifically designed for IoT applications. It contains an Atheros Microprocessor (MPU) holding a Linux based OpenWrt operating system. This Atheros MPU manages one Ethernet interface and one Wifi card, which make it a suitable device for IoT scenarios. The board has a USB-A port, micro-SD card slot, 20 digital input/output pins, a 16MHz crystal oscillator, a micro USB connection, an ICSP header, and 3 reset buttons.
A security analysis of the Arduino Yún shows that it contains many architectural flaws and since this AVR-based chip has limited resources compared with modern MCU and MPU based on ARM or x86 architectures, classical protections against memory corruption, such as stack overflow protection or memory layout randomization can not be easily deployed.
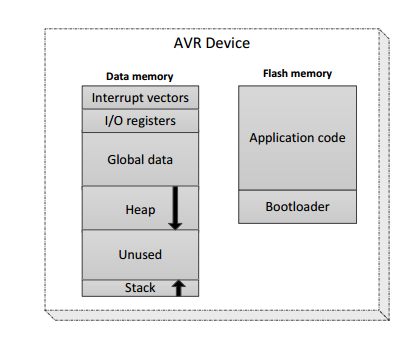
The key of this hack is to get the AVR to run out of RAM. Researchers wrote more and more data into memory until they reached the heap, the memory for control data.
Although the code you want to run is available in flash and it is immutable, recent researches proved that using Return-Oriented Programming (ROP) could inject code into the flash memory. These kind of ROP tricks came in handy for the researchers to write a worm.
Thus, the exploit uses code reuse attacks (Return Oriented Programming and return to-lib) to benefit from a memory corruption vulnerability. ArduWorm has also some infection capabilities and it can automatically spread through neighbor nodes.
During the last few years, malware in tablets and smartphone devices has become one of the main concerns of security researchers. According to Mcafee’s 2015 threat reports up to 1.2 million different malware pieces targeting mobile platforms were detected. A similar report published by the AV company PandaLabs, stated that during 2015 an average of 230.000 different samples were detected on a daily basis.
Researchers are developing ArduWorm as a proof of concept proven in their experimental setup, and they hope that it can motivate research in the design of defensive mechanisms for Arduino and IoT devices.
More details about this malware proof of concept are available at this research paper.